May/2025 Latest Braindump2go HPE6-A86 Exam Dumps with PDF and VCE Free Updated Today! Following are some new Braindump2go HPE6-A86 Real Exam Questions!
1.A network administrator is using Aruba Central to monitor network health. The dashboard indicates that a switch is experiencing high CPU utilization.
What should the administrator check first?
A. Increase the switch’s memory allocation
B. Check for excessive spanning-tree recalculations
C. Restart the switch
D. Disable SNMP polling
Answer: B
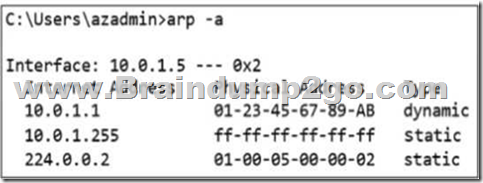
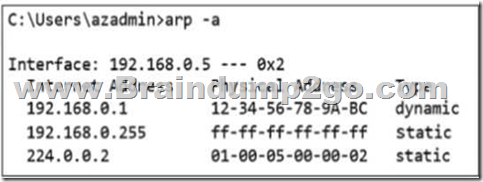
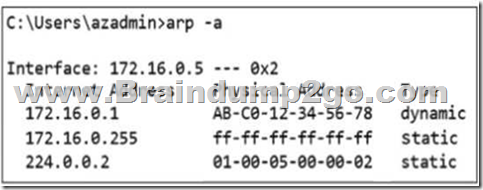
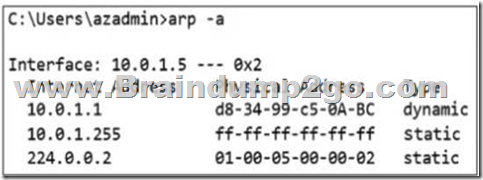
2.Which two tools can be used to troubleshoot switch connectivity issues? (Select TWO)
A. show vlan
B. traceroute
C. ping
D. netstat
Answer: BC
![image_thumb[1] image_thumb[1]](http://examgod.com/bdimages/May-2025Q81-Q101_A6CA/image_thumb1_thumb.png)
![image_thumb[3] image_thumb[3]](http://examgod.com/bdimages/May-2025Q81-Q101_A6CA/image_thumb3_thumb.png)
![image_thumb[1] image_thumb[1]](http://examgod.com/bdimages/New-ExamQ1-Q20_A8E9/image_thumb1_thumb.png)