May/2025 New Braindump2go 220-1202 Exam Dumps with PDF and VCE Free Updated Today! Following are some new Braindump2go 220-1202 Real Exam Questions!
Question: 1
SIMULATION
You are configuring a home network for a customer. The customer has requested the ability to access a Windows PC remotely, and needs all chat and optional functions to work in their game console.
INSTRUCTIONS
Use the drop-down menus to complete the network configuration for the customer. Each option may only be used once, and not all options will be used.
Then, click the + sign to place each device in its appropriate location.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Wireless AP LAN
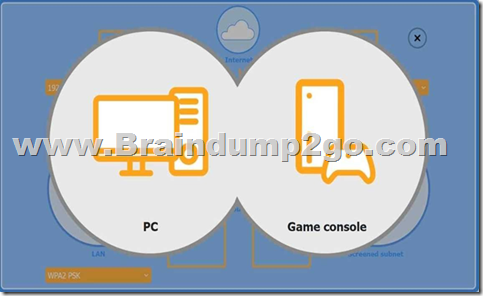
Firewall Screened Subnet
Answer: See explanation below.
The completed configuration:
1.Wireless AP (LAN side) 1. LAN IP: 192.168.10.1
2.Encryption: WPA2 PSK
2.Router (port-forward rule)
1.Allow TCP Any 3389
This forwards inbound RDP traffic (TCP/3389) from the Internet to the Windows PC, enabling Remote Desktop access.
3.Firewall (screened subnet side) 1. LAN IP: 10.100.0.1
4.Device placement PSK).
1.PC: place behind the router (where the port-forward rule points).
2.Game console: place on the Wireless AP (so it can use chat and extra services over WPA2
3.Firewall: place in front of the screened subnet (with its 10.100.0.1 IP facing that subnet).
Question: 2
A technician needs to provide remote support for a legacy Linux-based operating system from their Windows laptop. The solution needs to allow the technician to see what the user is doing and provide the ability to interact with the user’s session. Which of the following remote access technologies would support the use case?
A. VPN
B. VNC
C. SSH
D. RDP
Answer: B
Explanation:
Comprehensive and Detailed Explanation From Exact Extract:
The correct answer is VNC (Virtual Network Computing). VNC is a graphical desktop-sharing system that uses the Remote Frame Buffer protocol (RFB) to remotely control another computer. It is platform-independent and widely supported on Linux, which makes it ideal for providing interactive remote support for a Linux-based operating system. It allows the technician not only to view the remote desktop session but also to control it, fulfilling the need to see and interact with the user’s session.
A . VPN (Virtual Private Network) creates a secure tunnel to a network but does not provide desktop sharing or session control by itself.
C . SSH (Secure Shell) provides secure command-line access to Unix/Linux systems but does not offer graphical desktop interaction, which is a requirement in this case.
D . RDP (Remote Desktop Protocol) is primarily a Microsoft protocol, and although it can be made to work on Linux, it is not natively supported on legacy Linux systems, and thus less suitable than VNC in this scenario.
✅ CompTIA A+ 220-1102 Core 2 Objective Reference:
Objective 1.8 – Given a scenario, use features and tools of the operating system.
Under this objective, candidates are expected to be familiar with remote access technologies, including RDP, SSH, and VNC, and understand their appropriate uses and limitations on different platforms such as Windows and Linux.
Question: 3
A technician is attempting to join a workstation to a domain but is receiving an error message stating the domain cannot be found. However, the technician is able to ping the server and access the internet. Given the following information:
IP Address – 192.168.1.210
Subnet Mask – 255.255.255.0 Gateway – 192.168.1.1
DNS1 – 8.8.8.8
DNS2 – 1.1.1.1
Server – 192.168.1.10
Which of the following should the technician do to fix the issue?
A. Change the DNS settings.
B. Assign a static IP address.
C. Configure a subnet mask.
D. Update the default gateway.
Answer: A
Explanation:
Comprehensive and Detailed Explanation From Exact Extract:
The issue described—“domain cannot be found” despite the ability to ping the server and access the internet—indicates a DNS resolution problem, not a network connectivity issue. The workstation is currently using public DNS servers (8.8.8.8 and 1.1.1.1) which cannot resolve internal domain names, such as the ones used in Active Directory environments. To resolve this, the technician needs to change the DNS settings to point to the internal DNS server, which in most domain setups is the domain controller itself (likely 192.168.1.10 in this case).
Here’s the breakdown of the incorrect options:
B . Assign a static IP address: The IP is already assigned and functioning; the device can ping and reach the network and internet.
C . Configure a subnet mask: The subnet mask is appropriate for the network range (Class C /24).
D . Update the default gateway: The gateway is valid and allows internet access; this is not the issue.
✅ CompTIA A+ 220-1102 Core 2 Objective Reference:
Objective 1.8 – Given a scenario, use features and tools of the operating system.
Under this objective, candidates must know how to troubleshoot OS-based network configurations, including proper DNS settings in domain environments.
Question: 4
A network technician notices that most of the company’s network switches are now end-of-life and need to be upgraded. Which of the following should the technician do first?
A Implement the change
B. Approve the change.
C. Propose the change.
D. Schedule the change.
Answer: C
Explanation:
In a structured change-management process, the very first step is to propose (or formally request) the change via a Request for Change (RFC). This ensures stakeholders review the need, assess risks, and determine the priority before any approvals, scheduling, or implementation occur.
Question: 5
MFA for a custom web application on a user’s smartphone is no longer working. The last time the user remembered it working was before taking a vacation to another country. Which of the following should the technician do first?
A. Verify the date and time settings.
B. Apply mobile OS patches.
C. Uninstall and reinstall the application.
D. Escalate to the website developer.
Answer: A
Explanation:
Time-based one-time password (TOTP) MFA apps rely on accurate clock synchronization. Traveling can desynchronize the device’s clock, causing generated codes to be invalid. Ensuring the smartphone’s date/time (and time zone) are correct will typically restore MFA functionality immediately.
Question: 6
Which of the following is found in an MSDS sheet for a battery backup?
A. Installation instructions
B. Emergency procedures
C. Configuration steps
D. Voltage specifications
Answer: B
Explanation:
A Material Safety Data Sheet (MSDS) provides critical safety and handling information for hazardous materials – in this case, the battery’s chemicals. It includes emergency procedures (first-aid measures, fire-fighting steps, spill containment), ensuring responders know how to act safely in an incident.
Question: 7
The screen of a previously working computer repeatedly displays an OS Not Found error message when the computer is started. Only a USB drive, a keyboard, and a mouse are plugged into the computer. Which of the following should a technician do first?
A. Run data recovery tools on the disk.
B. Partition the disk using the GPT format.
C. Check boot options.
D. Switch from UEFI to BIOS.
Answer: C
Explanation:
An “OS Not Found” error most commonly indicates the system isn’t booting from the correct device. Verifying and correcting the boot order (ensuring the internal hard drive is prioritized over USB or other entries) is the quickest first step before making any changes to the disk or firmware settings.
Question: 8
A security administrator teaches all of an organization’s staff members to use BitLocker To Go. Which of the following best describes the reason for this training?
A. To ensure that all removable media is password protected in case of loss or theft
B. To enable Secure Boot and a BIOS-level password to prevent configuration changes
C. To enforce VPN connectivity to be encrypted by hardware modules
D. To configure all laptops to use the TPM as an encryption factor for hard drives
Answer: A
Explanation:
BitLocker To Go is specifically designed to encrypt removable drives (USB flash drives, external HDDs). Training staff on its use guarantees that any data stored on such media requires a password (or recovery key) to access, protecting sensitive information if the device is lost or stolen.
Question: 9
Which of the following is used to detect and record access to restricted areas?
A. Bollards
B. Video surveillance
C. Badge readers
D. Fence
Answer: C
Explanation:
Badge readers authenticate and log each entry attempt – recording who accessed (or tried to access) a secured area and when. This audit trail is essential for monitoring and reviewing access to restricted zones.
Question: 10
An administrator received an email stating that the OS they are currently supporting will no longer be issued security updates and patches. Which of the following is most likely the reason the administrator received this message?
A. Support from the computer’s manufacturer is expiring.
B. The OS will be considered end of life.
C. The built-in security software is being removed from the next OS version.
D. A new version of the OS will be released soon.
Answer: B
Explanation:
When an operating system reaches end of life (EOL), the vendor ceases issuing security updates and patches. Administrators are notified so they can plan upgrades or migrations before support ends.
Question: 11
Which of the following is the best way to distribute custom images to 800 devices that include four device vendor classes with two types of user groups?
A. Use xcopy to clone the hard drives from one to another.
B. Use robocopy to move the files to each device.
C. Use a local image deployment tool for each device.
D. Use a network-based remote installation tool.
Answer: D
Explanation:
A network-based remote installation tool (such as Windows Deployment Services, MDT, or a similar solution) scales efficiently across hundreds of devices with varying hardware and user configurations. It allows you to segment deployments by vendor classes and user groups, automate imaging processes, and manage version control centrally – far more effectively than one-to-one cloning or
file-copy methods.
Question: 12
Which of the following types of social engineering attacks sends an unsolicited text message to a user’s mobile device?
A. Impersonation
B. Vishing
C. Spear phishing
D. Smishing
Answer: D
Explanation:
Smishing is the act of sending fraudulent messages via SMS or other texting platforms to trick users into revealing sensitive information or clicking malicious links. This distinguishes it from phishing over email (spear phishing), voice calls (vishing), or in-person deception (impersonation).
Question: 13
A user reports some single sign-on errors to a help desk technician. Currently, the user is able to sign in to the company’s application portal but cannot access a specific SaaS-based tool. Which of the following would the technician most likely suggest as a next step?
A. Reenroll the user’s mobile device to be used as an MFA token.
B. Use a private browsing window to avoid local session conflicts.
C. Bypass single sign-on by directly authenticating to the application.
D. Reset the device being used to factory defaults.
Answer: B
Explanation:
Single sign-on issues that affect only a specific application often stem from stale or conflicting session data in the user’s browser. Launching a private (incognito) window ensures a fresh session without cached cookies or tokens, which can resolve access to the SaaS tool without affecting other configurations.
Question: 14
A technician verifies that a malware incident occurred on some computers in a small office. Which of the following should the technician do next?
A. Quarantine the infected systems.
B. Educate the end users.
C. Disable System Restore.
D. Update the anti-malware and scan the computers.
Answer: A
Explanation:
Once an incident is confirmed, the immediate priority is containment. Isolating (quarantining) the infected machines prevents the malware from spreading to other systems or exfiltrating data, enabling safe analysis and remediation.
Question: 15
Which of the following is a Linux command that is used for administrative purposes?
A. runas
B. cmcl
C. net user
D. su
Answer: D
Explanation:
The su (substitute user) command is a standard Linux utility that allows an administrator to assume another user’s identity – most commonly switching to the root account for elevated privileges. It’s an essential tool for administrative tasks on Unix and Linux systems.
Question: 16
A user recently installed an application that accesses a database from a local server. When launching the application, it does not populate any information. Which of the following command-line tools is the best to troubleshoot the issue?
A. ipconfig
B. nslookup
C. netstat
D. curl
Answer: C
Explanation:
netstat reveals active network connections and listening ports on the local machine. By using it, you can confirm that the application has successfully opened (or attempted) a connection to the database server’s port, verify the remote server’s address and port, and detect any failed or hanging TCP sessions that would prevent data retrieval.
Question: 17
A small office reported a phishing attack that resulted in a malware infection. A technician is investigating the incident and has verified the following:
● All endpoints are updated and have the newest EDR signatures.
● Logs confirm that the malware was quarantined by EDR on one system.
● The potentially infected machine was reimaged.
Which of the following actions should the technician take next?
A. Install network security tools to prevent downloading infected files from the internet.
B. Discuss the cause of the issue and educate the end user about security hygiene.
C. Flash the firmware of the router to ensure the integrity of network traffic.
D. Suggest alternate preventative controls that would include more advanced security software.
Answer: B
Explanation:
With technical controls updated, EDR signatures current, and the infected system reimaged, the next step is to address the human factor. Educating the user on how to recognize phishing attempts and follow safe practices helps prevent recurrence and strengthens the organization’s overall security posture.
Question: 18
Which of the following describes a vulnerability that has been exploited before a patch or remediation is available?
A. Spoofing
B. Brute-force
C. DoS
D. zero-day
Answer: D
Explanation:
A zero-day vulnerability refers to a security flaw that is actively exploited by attackers before the software vendor has released a patch or remediation – meaning defenders have “zero days” to prepare once the exploit becomes known.
Question: 19
SIMULATION
You have been contacted through the help desk chat application. A user is setting up a replacement SOHO router. Assist the user with setting up the router.
INSTRUCTIONS
Select the most appropriate statement for each response. Click the send button after each response to continue the chat.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Answer: See
explanation below.
First Chat Response: When the user mentions setting up a new router, the best initial response to maintain a helpful and professional tone is:
●Select reply: “I am happy to assist you today.”
Second Chat Response: When the user states that they need to set up basic security settings:
●Select reply: “Is this the first router in your office?”
Third Chat Response: After learning it’s a replacement router and the user is logged into the router’s web page:
●Select reply: “The first thing you need to do is change the default password.”
Fourth Chat Response: For the response about password settings:
●Select reply: “Create a new password with an uppercase, a lowercase, and a special character.”
Fifth Chat Response: When the router prompts to reboot:
●Select reply: “Yes, reboot please.”
Question: 20
A help desk technician is setting up speech recognition on a Windows system. Which of the following settings should the technician use?
A. Time and Language
B. Personalization
C. System
D. Ease of Access
Answer: D
Explanation:
Windows places speech recognition and other accessibility features under the Ease of Access settings. From there, you can configure Speech options – including enabling Windows Speech Recognition and adjusting its settings – so that users relying on voice input can operate the system effectively.
Question: 21
A user receives a new personal computer but is unable to run an application. An error displays saying that .NET Framework 3.5 is required and not found. Which of the following actions is the best way to resolve this issue?
A. Resolve the dependency through the ‘Turn Windows features on or off’ menu.
B. Download the dependency via a third-party repository.
C. Ignore the dependency and install the latest version 4 instead.
D. Forward the trouble ticket to the SOC team because the issue poses a great security risk.
Answer: A
Explanation:
Windows includes .NET Framework 3.5 as an optional feature. Enabling it via Control Panel → Programs and Features → Turn Windows features on or off ensures the OS installs the correct version directly from Microsoft without relying on untrusted sources or skipping needed dependencies.
Question: 22
An employee is using a photo editing program. Certain features are disabled and require a log-in, which the employee does not have. Which of the following is a way to resolve this issue?
A. License assignment
B. VPN connection
C. Application repair
D. Program reinstallation
Answer: A
Explanation:
When features in an application are disabled pending a login, it typically indicates those capabilities are controlled by the software’s licensing system. Assigning (or activating) the proper license entitles the user to those premium features, restoring full functionality without unnecessary repair or reinstall steps.
Question: 23
A technician is deploying mobile devices and needs to prevent access to sensitive data if the devices are lost. Which of the following is the best way to prevent unauthorized access if the user is unaware that the phone is lost?
A. Encryption
B. Remote wipe
C. Geofencing
D. Facial recognition
Answer: A
Explanation:
Full-disk (or device) encryption ensures that, even if a lost mobile device is physically accessed by an unauthorized party, its stored data remains inaccessible without the correct decryption credentials. This protection is automatic and continuous, safeguarding data at rest regardless of whether the user realizes the device is missing or not. Remote wipe can remove data if triggered, but it requires the device to be online and the user (or admin) to initiate the wipe—whereas encryption is always in effect.
Question: 24
Which of the following is the quickest way to move from Windows 10 to Windows 11 without losing data?
A. Using gpupdate
B. Image deployment
C. Clean install
D. In-place upgrade
Answer: D
Explanation:
An in-place upgrade directly installs Windows 11 over the existing Windows 10 installation, preserving user files, applications, and settings. It’s much faster than capturing and redeploying an image, and it avoids the data loss risk of a clean install.
Question: 25
Technicians are failing to document user contact information, device asset tags, and a clear description of each issue in the ticketing system. Which of the following should a help desk management team implement for technicians to use on every call?
A. Service-level agreements
B. Call categories
C. Standard operating procedures
D. Knowledge base articles
Answer: C
Explanation:
Standard operating procedures (SOPs) define consistent, step-by-step guidelines that technicians must follow – such as capturing user contact details, asset tags, and detailed issue descriptions on every ticket. Implementing SOPs ensures thorough and uniform documentation across all calls.
Question: 26
An application’s performance is degrading over time. The application is slowing, but it never gives an error and does not crash. Which of the following tools should a technician use to start troubleshooting?
A. Reliability history
B. Computer management
C. Resource monitor
D. Disk
Answer: C
Explanation:
Resource Monitor provides real-time insights into CPU, memory, disk, and network usage by process. By observing which resources steadily increase or become bottlenecks over time, a technician can pinpoint leaks (e.g., memory), I/O contention, or other performance issues driving the slowdown.
Question: 27
Which of the following filesystem types does the Linux OS use?
A. exFAT
B. APFS
C. ext4
D. NTFS
Answer: C
Explanation:
ext4 (Fourth Extended Filesystem) is the default filesystem for most Linux distributions. It offers improved performance, reliability, and support for large volumes and files compared to its predecessors (ext2/ext3).
Question: 28
Which of the following methods would make data unrecoverable but allow the drive to be repurposed?
A. Deleting the partitions
B. Implementing EFS
C. Performing a low-level format
D. Degaussing the device
Answer: C
Explanation:
A low-level format (more accurately, a secure erase that overwrites all sectors with zeroes or random data) effectively wipes all data on the drive, making previous content unrecoverable while leaving the drive’s structure intact for reuse. Unlike degaussing – which destroys the drive’s magnetic media and renders it unusable – overwriting allows the drive to be repurposed safely.
Question: 29
After a recent mobile OS upgrade to a smartphone, a user attempts to access their corporate email, but the application does not open. A technician restarts the smartphone, but the issue persists.
Which of the following is the most likely way to resolve the issue?
A. Updating the failed software
B. Registering the smartphone with an MDM solution
C. Installing a third-party client
D. Clearing the cache partition
Answer: A
Explanation:
After a major OS upgrade, existing applications often require updates to maintain compatibility with new APIs and system libraries. Updating the corporate email app to its latest version ensures it’s built against the updated OS and can launch properly.
Question: 30
Users are reporting that an unsecured network is broadcasting with the same name as the normal wireless network. They are able to access the internet but cannot connect to the file share servers. Which of the following best describes this issue?
A. Unreachable DNS server
B. Virtual local area network misconfiguration
C. Incorrect IP address
D. Rogue wireless access point
Answer: D
Explanation:
A rogue access point mimics the legitimate SSID, allowing clients to connect (often with internet access via its own uplink) but isolating them from internal resources like file shares. This behavior matches the symptoms – users join what appears to be the corporate WLAN but can’t reach internal servers.
Question: 31
A computer technician is implementing a solution to support a new internet browsing policy for a customer’s business. The policy prohibits users from accessing unauthorized websites based on categorization. Which of the following should the technician configure on the SOHO router?
A. Secure management access
B. Group Policy Editor
C. Content filtering
D. Firewall
Answer: C
Explanation:
Content filtering on a SOHO router lets you block or allow websites based on their categories (e.g., social media, gambling, news). By defining which categories are unauthorized, the router enforces the browsing policy at the network edge, preventing users from reaching disallowed sites.
Resources From:
1.2024 Latest Braindump2go 220-1202 Exam Dumps (PDF & VCE) Free Share:
https://www.braindump2go.com/220-1202.html
2.2024 Latest Braindump2go 220-1202 PDF and 300-630 VCE Dumps Free Share:
https://drive.google.com/drive/folders/19K12fblZo5_FUOVCi4n5Meyi8T5M3YFx?usp=sharing
3.2023 Free Braindump2go 220-1202 Exam Questions Download:
https://www.braindump2go.com/downloadable/download/sample/sample_id/7057/
Free Resources from Braindump2go,We Devoted to Helping You 100% Pass All Exams!
![image_thumb[1] image_thumb[1]](http://examgod.com/bdimages/May-2025Q81-Q101_A6CA/image_thumb1_thumb.png)
![image_thumb[3] image_thumb[3]](http://examgod.com/bdimages/May-2025Q81-Q101_A6CA/image_thumb3_thumb.png)